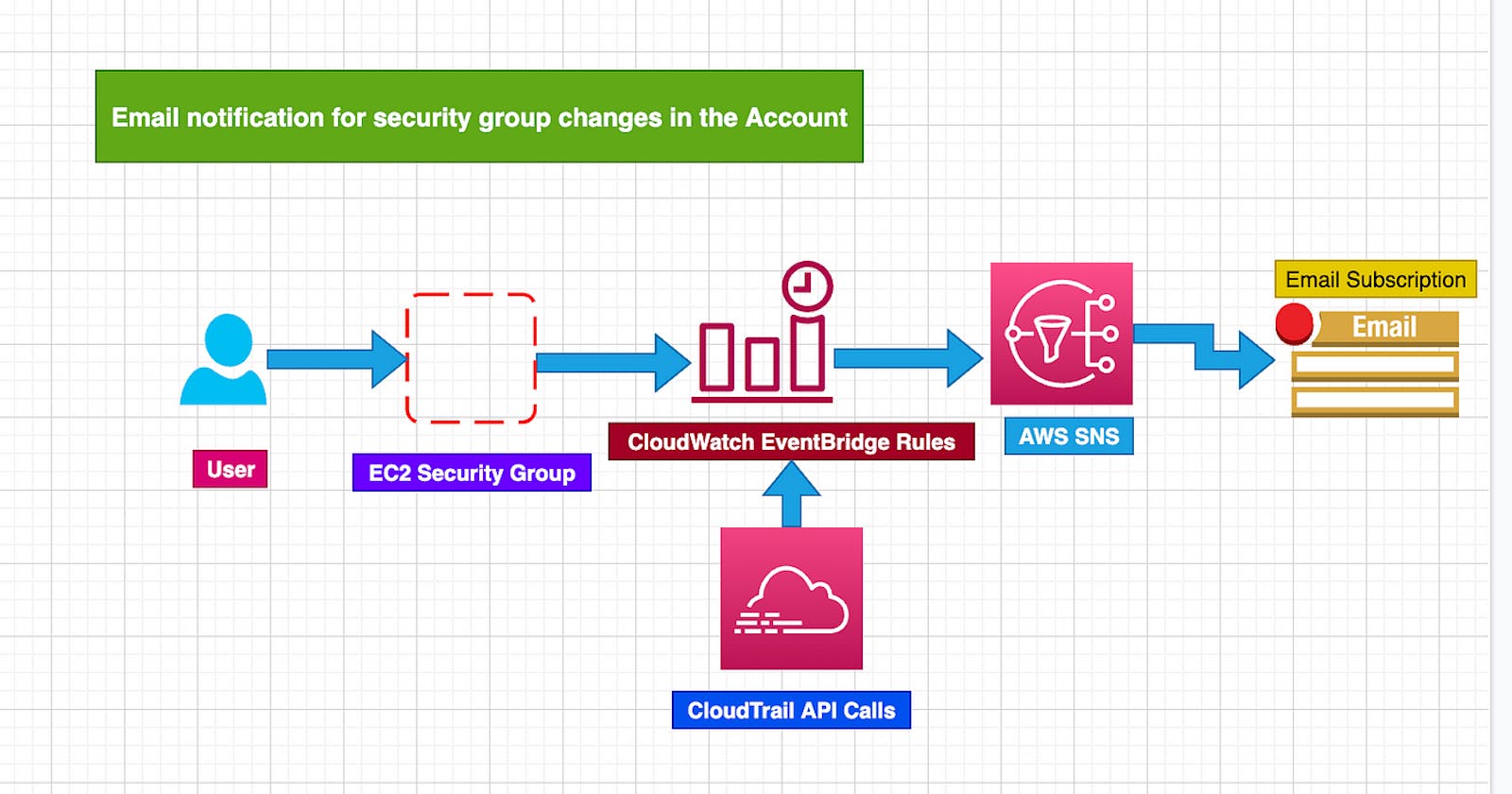
Monitoring Security Group Changes in AWS Organizations using CloudTrail, CloudWatch, and SNS
1. Introduction
Security is a paramount concern when managing AWS resources, especially when handling changes to Security Groups within an organization. This article provides insights into how to monitor these changes using AWS CloudTrail, AWS CloudWatch, and Amazon Simple Notification Service (SNS) across an AWS Organization.
2. Overview of AWS CloudTrail
AWS CloudTrail is a service that logs, continuously monitors, and retains account activity related to actions across your AWS infrastructure. When it comes to Security Groups, any changes made generate an API call, which is logged by CloudTrail. This capability of CloudTrail is essential to our process of monitoring changes.
3.Overview of AWS Security Group
A Security Group in AWS acts as a virtual firewall for your instance to control inbound and outbound traffic. Security Groups are essential for maintaining the robust security of your AWS resources, as they control the traffic that's allowed to reach the AWS instance. This makes it a crucial aspect to monitor for any changes to maintain the integrity and the security posture of your AWS infrastructure
4. Overview of AWS CloudWatch
AWS CloudWatch is a service designed to provide robust monitoring for AWS resources and applications in real time. With its Events feature (currently transitioning to Amazon EventBridge), it reacts to changes to AWS resources, making it a key component of our security monitoring setup.
5. Overview of Amazon SNS
Amazon Simple Notification Service (SNS) is a managed service that provides message delivery from publishers to subscribers (also known as producers and consumers). This service will be responsible for sending notifications when CloudTrail logs a specific event related to security group changes.
6. Monitoring Security Group Changes: A Step-by-Step Guide
Step 1: Set Up AWS CloudTrail
Ensure CloudTrail is configured to log events in all regions and that management events are included in its logging. For AWS Organizations, an organization trail can be created to apply to all accounts within the organization.
Step 2: Set Up Amazon SNS
Create a new SNS topic and configure subscribers who will receive notifications Confirm the subscription to the SNS topic.These could be email addresses, SMS messages, or even AWS Lambda functions.
Step 3: Set Up Amazon CloudWatch Events
Create a rule in CloudWatch Events to match events from CloudTrail, then route those events to the SNS topic created in Step 2. The rule may look like this:
{
"detail-type": [
"AWS API Call via CloudTrail"
],
"detail": {
"eventSource": [
"ec2.amazonaws.com"
],
"eventName": [
"AuthorizeSecurityGroupIngress",
"AuthorizeSecurityGroupEgress",
"RevokeSecurityGroupIngress",
"RevokeSecurityGroupEgress",
"CreateSecurityGroup",
"DeleteSecurityGroup"
]
}
}
Step 4: Create the Rule
In the CloudWatch Events console, create a new rule. Paste in the event pattern above, and for the targets, choose the SNS topic you created earlier. Now, when any of the specified events occur, CloudWatch Events will send a message to your SNS topic, which will in turn send a notification to any subscribers.Remember to set permissions correctly for all these services to interact with each other.
7. Conclusion
In conclusion, AWS provides robust tools for monitoring and alerting on changes to security group configurations. By using AWS CloudTrail, CloudWatch, and SNS together, organizations can set up real-time alerts for security group changes, thereby enhancing their security posture and their ability to respond swiftly to any undesired changes.